By Dr. Athanasios Staveris-Polykalas
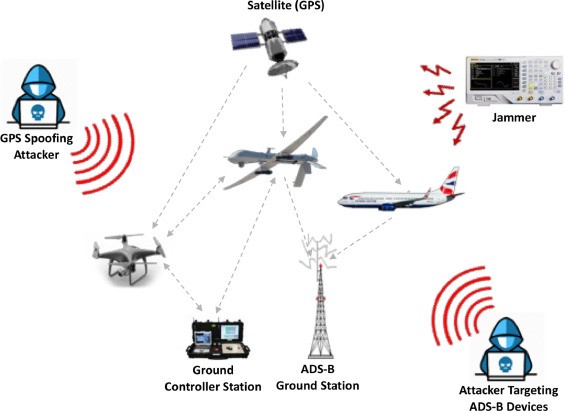
In today’s technologically charged era, the proliferation of Unmanned Aerial Vehicles (UAVs) or drones is undeniable. From delivery services to wildlife monitoring, and from filmmaking to defense operations, UAVs are reshaping our world in myriad ways. Yet, with this accelerated integration comes a myriad of cybersecurity threats. The task at hand is twofold: understanding these vulnerabilities and fortifying our UAVs against them. This essay embarks on a deep dive into the cybersecurity challenges facing UAV operations and offers guidance on building a robust defense mechanism.
Understanding the Vulnerabilities
- Accidental Mishaps: One common misconception is that all threats are malicious. In reality, many UAV incidents arise from non-malicious yet unintended actions, such as system errors or operator mistakes. Such unintentional threats can disrupt a UAV’s path, causing collisions or damages.
- Malicious Intrusions: This is the deliberate exploitation of a UAV’s system. From hijacking the drone for criminal purposes to data breaches, these are actions carried out with harmful intent.
- Militaristic Impacts: On the defense front, a compromised UAV can be a significant asset for adversarial forces, enabling espionage, targeted attacks, or data extraction.
Guarding Against Unauthorized Control
Unauthorized control is a substantial threat in UAV operations. Ensuring UAVs are resilient against unsanctioned access is paramount.
Robust Communication Channels: The very essence of a UAV lies in its remote operability. Thus, the communication link between the drone and its control station becomes its lifeline. Strengthening this link with encrypted communications ensures that external entities cannot easily intercept or manipulate it.
Authentication Protocols: Implementing sophisticated authentication measures reduces the risk of unauthorized access. Advanced methods, such as biometric authentication or cryptographic keys, can ensure that only trusted individuals can assume control.
System Updates and Vulnerability Management: UAV software, like any other, is susceptible to flaws. Regularly updating the software and routinely scanning for vulnerabilities helps in preempting potential attacks.
Protection of Data: An Intrinsic Requirement
UAVs are data goldmines. They collect vast amounts of data, be it visual, thermal, or telemetry. This data, if accessed illicitly, can lead to severe consequences.
Encryption: Data, both in storage (on the UAV) and in transit (during transmission), should be encrypted using state-of-the-art cryptographic techniques. This ensures that even if data is intercepted, it remains gibberish to unauthorized entities.
Regulated Access: Implementing access controls, such as role-based access rights, can prevent unauthorized data access or manipulation. Only individuals with the required clearance level should access specific sets of data.
Data Retention Policies: Storing data indefinitely increases its exposure risk. Instituting strict data retention policies, where data is stored only for the required duration and then securely deleted, can minimize potential threats.
Holistic Security Approach
Beyond individual measures, a UAV’s security is about the ecosystem. Adopting a holistic security approach encompasses not just the technology but also the people and processes involved.
Regular Training: All personnel associated with UAV operations should undergo regular training. Keeping them updated on the latest threats and countermeasures is crucial.
Collaborative Defense: Cybersecurity is a constantly evolving field. Collaborating with external security experts and organizations can provide insights into emerging threats and defense methodologies.
Comprehensive Policies: Establishing well-documented security and operational policies provides a clear roadmap for all stakeholders. These policies should be reviewed and updated at regular intervals.
Conclusion
The dynamic world of UAVs offers limitless potential but also presents unique cybersecurity challenges. As these drones increasingly become an integral part of our infrastructure, ensuring their security is not just a technical necessity but also a societal obligation. By combining cutting-edge technologies, best practices, and continuous vigilance, we can harness the benefits of UAVs while minimizing the associated risks, steering towards a secure and innovative future.